Why your enterprise needs a Mobile Threat Defense (MTD) in place. Today!
from Cyber Security News https://ift.tt/39abWru
Live Player 3.2 extension and toolbar is a corrupt browser application that ruins Firefox, Google Chrome and Internet explorer, etc. The Live Player 3.2 virus comes as a free TV channel player which offers its user watch various international TV shows and programs without paying anything. But soon after this program has been installed, you,ll
Why your enterprise needs a Mobile Threat Defense (MTD) in place. Today!
The National Institute for Standards and Technology (NIST) released a report outlining best practices in building the cybersecurity workforce through regional partnerships.
Originally introduced in 2004 as a videogame simulation spinoff, an escape room is a game where teams collaboratively piece together clues, solve puzzles and riddles in order to get out of a room in a given period of time. Time is of the essence, and it is critical that team members work together to win.
Registration is now open for the spring season of the National Cyber League (NCL) competition.
Deltek, a provider of software and solutions for project-based businesses, appointed Caleb Merriman as its Vice President and Chief Information Security Officer (CISO).
The National Association of Corporate Directors (NACD) and the Internet Security Alliance (ISA) released a new, updated Director’s Handbook on Cyber-Risk Oversight, a guidebook to help boards navigate cyber-risk oversight.
The concept of hacking as a viable career has become a reality, with 18% of survey respondents describing themselves as full-time hackers, searching for vulnerabilities and making the internet safer for everyone.
Michael S. Oberlaender, a CISO and CSO, author and subject matter expert who has worked in global executive level security roles and in IT both in the U.S. and EU for more than 25 years, has released a new book on CISO leadership.
Cybersecurity teams continue to struggle with hiring and retention, and very little improvement has been achieved in these areas since last year, according to new global research from ISACA that identifies current workforce challenges and trends in the cybersecurity field.
Cisco's sixth annual CISO Benchmark Report has found that the average company uses more than 20 security technologies, which makes managing a multi-vendor environment challenging.
Eric Clay, System Director of Public Safety and Security, has been promoted to Chief Security Officer at CoxHealth.
Rick Howard will join the CyberWire executive team as CSO and Chief Analyst.
The University of Alabama will offer students a new degree program in the field of cybersecurity beginning this fall.
George Mason University’s Volgenau School of Engineering announces the creation of the Department of Cyber Security Engineering, the first of its kind in the country.
Exabeam announced the Exabeam Cybersecurity Scholarship Program, an initiative designed to support the next generation of professionals in pursuing an education and career in the security field.
IT security practitioners are aware of good habits when it comes to strong authentication and password management, yet often fail to implement them due to poor usability or inconvenience, says the 2020 State of Password and Authentication Security Behaviors Report.
ISC West, the largest security industry trade show in the U.S., will be held next month at the Sands Expo Convention Center in Las Vegas – but with the outbreak of the novel coronavirus in China, a few key changes will be made to this year’s event.
Veeam® Software, a provider of backup solutions that deliver Cloud Data Management™, announced that Gil Vega has been appointed Chief Information Security Officer (CISO).
NETSCOUT Threat Intelligence saw 8.4 million Distributed Denial of Service (DDoS) attacks last year alone: 23,000 attacks per day, 16 every minute.
62% of CISOs think the global cybersecurity talent shortage will get worse over the next five years, according to Global Snapshot: The CISO in 2020, a report that explores the role and demographics of CISOs.
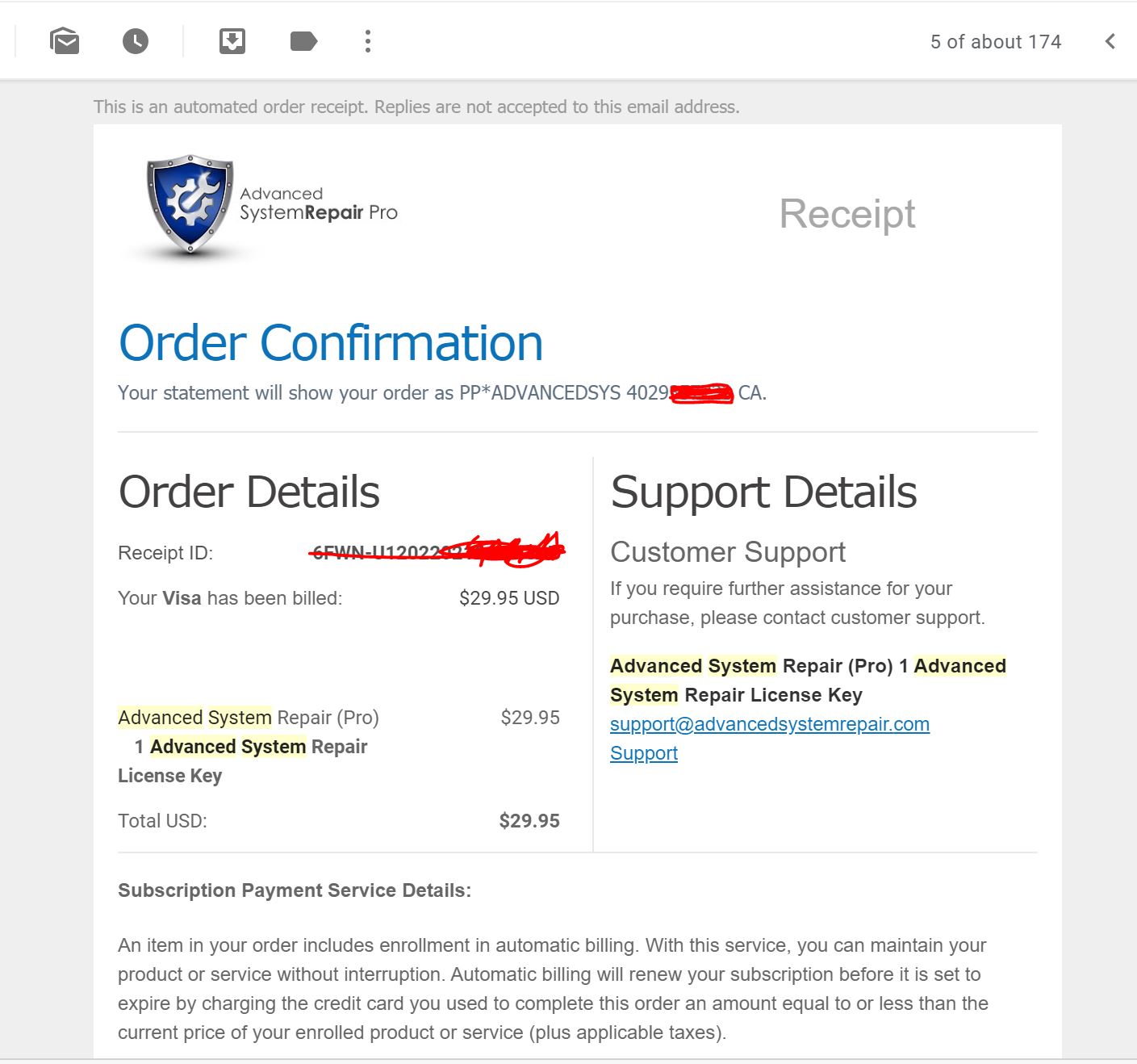
When it comes to solving computer issues there aren’t many options out there for those who aren’t “tech savvy”. It seems like you’re either stuck with a slow computer or stuck with a huge repair bill from a shop. Enter Advanced System Repair Pro: this is a software program designed to simplify computer maintenance tasks in a way that is easy enough for the average computer user to understand and use.
Does this software do what it claims it can do? Is it worth your time and money? Read our full Advanced System Repair Pro review below to find out the results of our real world testing.
For this review I personally purchased the software to see what the billing and purchase process is like. I was not given this software to review or asked to write this review – I am doing it voluntarily and with my own money.
Advanced System Repair Pro is a winner in terms of an all-in-one system maintenance solution. This product is very well documented and has undergone a series of third party tests proving performance increases of 40% for boot times, video conferences, browser performance, and more (data supplied by third party Tolly in their extensive report which you can read here).
It is also a member of several third party ethical app groups such as AppEsteem. Overall it’s a very safe product with a great Better Business Bureau rating and support. The results you get will vary by computer, but most people looking for a product like this will get a pretty sizable boost to their computer performance.
Visit Advaned System Repair Pro Home Page
Advanced System Repair Pro is full of features designed to help you get the most performance out of a lagging computer. Most of these functions will be unknown to the average user, but let’s take a look at everything it claims to do:
Advanced System Repair Pro is one of the most certified software tools I’ve reviewed. They have several trust certifications from third party organizations such as AppEsteem, CleanApps.org, Tolly, and are “AAA” rated Checkmark Certified by West Coast Labs.
I really like the report from Tolly that showcases a real world result produced by a third party company. In the report they detail the results of using ASRP on several Windows systems and how much each system improved upon running the software.
It’s notable that the biggest impact on user perception and improvement from these third party tests is in Windows boot speed.
It’s also good to note that TrustPilot has 4,081 user reviews with an average rating of 4.5/5 as of this writing. Most of the complaints that I see online are about the recurring billing cycle that they use. However I find these complaints a bit outrageous as it is very clearly stated on their website that they do this. If you don’t want to keep paying for the product I highly recommend simply sending an email to the billing department right after purchase to ensure that you don’t get rebilled.
When I purchased the software for myself, the billing process was straightforward. People should be aware of an upsell for Advanced Privacy Guard that pops up when purchasing the software. You can decline this. Again, it’s very clearly marked although if you’re in a rush you might miss it. Take your time and read the prompts before clicking. I tested PayPal and Credit Card, and both worked as promised with no hidden fees. If you use PayPal it’s easier to cancel the recurring billing on your end without the need to contact ASRP.
I ran ASRP on my Windows 10 Surface Pro 4 tablet. This tablet hasn’t been in use that long so it’s admittedly not the best test system, but I also thought it would be interesting to see if it could even improve the performance of a system that is relatively new (around 1 year in use). The Tolly report mentioned above gives even more detail about the the software performs on older machines.
When I ran the scan there were no false positives, which I thought was nice. It did not detect any malware, because I don’t have any on this system. This is important to note because in the past there were some unsavory software tools that would give false reports of malware in order to incite the user to purchase. With this software you do not need to worry about that at all.
Overall I highly recommend that you inspect all the changes the software wants to make before you fix them all in one go. For instance, by default it will delete all your browser cookies and saved passwords. I do not see saving passwords on your system as a security threat as they are usually well encrypted and if you delete these it might cause you a big headache.
The biggest surprise was 5 gig of “junk files” which are essentially just temporary files that are not necessary to keep around. 5 gig is a lot, especially on a hard drive that is only 128 gig total (half of which is typically used up by Windows and essential software anyway!). In my case it was mostly coming from Driver Packages and Memory Dumps.
I do not recommend deleting driver packages as this can hurt your ability to install plug and play devices in the future. As it’s only 1.71 gb, I do not need to delete it anyway.
Memory dumps are safe to delete – these are just crash records from when Windows stops running.
The startup optimizer can be especially helpful for people who are experiencing slow bootups. This will help you analyze which software is hogging resources when you turn on your PC.
I don’t have much software installed on this computer, but you can see that Microsoft OneDrive and Adobe Creative Cloud are taking up a lot of my resources on boot. However, since I need these programs I will leave them alone. In your case you may have unnecessary software loading on bootup. Experiment with these to see what you can prune.
It was also interesting to note how many of my system hardware drivers were out of date. Updating drivers can have a noticeable impact on system stability and speed, especially for video drivers. In my case there were 39 drivers that I could update, ranging from my Intel camera to my Microsoft Surface Display.
“While some system clean-up utilities may focus on a given area, such as driver updates, system registry, or disk fragmentation, ASR provides a complete system repair capability; including a malware detection and removal engine that has, separately to this test, been awarded Checkmark Certification in its own right.” — West Coast Labs
There were a few times while testing the software that I couldn’t quite figure out how to turn off a feature. The software interface could definitely benefit from some streamlining, but overall it’s still pretty good. On a positive note there is an incredible amount of detail hidden in the interface – you can drill down and see exactly what files and folders the software is cleaning up. Compared to CCleaner it’s MUCH better in this regard.
When contacting support via email to cancel my recurring subscription, they responded within an hour and a half. There is no obvious phone number to contact them but this is pretty typical. Still it will knock some points off in our review as we like software to have a phone number. However, it’s not a deal breaker as this is not a very expensive product and you can still get in touch fairly quickly via email.
Pros
Cons
Advanced System Repair is a great option for those with older machines that want to squeeze a bit more life out them before plunking down money on a new system.
Those with Windows installations (this software doesn’t work on Macs) will probably be very happy with the amount of hard disk space they can recover and the improvements they see in boot speed. Obviously all computers are different and some people will see more improvements than others, and this is noted on the ASRP website as well.
So, if you have had it with your computer’s performance and want to give it a second chance, you might seriously benefit from giving this software a try.
Visit Advaned System Repair Pro Home Page
The University of South Florida announced the appointment of J. Michael (Mike) McConnell, retired U.S. Navy vice admiral and former director of the National Security Agency (NSA), as executive director of Cyber Florida.
Legislation introduced by representatives from the House Committee on Homeland Security would authorize a new grant program at DHS to address cybersecurity vulnerabilities on state and local government networks.
When it comes to computer security these days, it is incredibly important to ensure that you are running reputable software to ensure your data is protected at all times. I get a lot of people emailing me and asking about Malwarebytes vs Avast, and which one is better for them.
While both programs are really good, they are not completely direct competitors. Instead, they offer protections against different types of threats. Let’s take a look at each program and their pros and cons so you can decide for yourself if you want one or the other, or even both.
Malwarebytes Corporation is an American-based international computer security software firm that started in 2006. Their initial offering of Malwarebytes started out as a pure malware removal software tool, but over the years it has evolved into a fully featured security solution for PCs, Macs, and Androids. As far as complete protection, Malwarebytes Premium is all you really need for your computer, eliminating the need for additional antivirus software. According to the Malwarebytes website, with the release of Malwarebytes Premium 3, it’s now a complete solution:
“Malwarebytes 3 Premium is our best security offering to date and can serve as the computer’s primary source of software-based protection.” –Malwarebytes.com
This is especially true with the introduction of the free Windows Defender that is extremely good at antivirus tasks.
We recently wrote up a Malwarebytes Review and we actually gave it a perfect score because we feel it is an excellent piece of software and we use it on our own computers.
Avast is a Czech company that has been around since 1988 and currently has over 1000 employees nationwide. They are a big player in the computer security field. They have come out with a suite of different computer protection programs over the years, however the most important of the bunch is Avast Internet Security as well as Premier and Ultimate which are upgrades with more features.
Avast Antivirus got a facelift for 2018 and features a dark skinned theme that is clear and easy to read. This new update features a multitude of updates and is capable of being a fully featured internet security tool for your PC, Mac, or phone. Depending on which version you get you will get various tiers of features. We always recommend getting the best you can afford, however we think that the Internet Security and Premier versions are adequate protections unless you want the VPN and password storage feature that the Ultimate version provides.
As far as how Avast fares, it does extremely well in vigorous malware, virus, and phishing site tests. PC Mag gave it an extremely good writeup as well as our experience with the software. If you are comparing the paid versions it seems Avast is neck and neck with Malwarebytes.
This was a tough call. For now I recommend Malwarebytes Premium as a front line defense. It’s a bit more lightweight and the protection is just as good, and it’s cheaper.
However, Avast is also very good and they offer a couple more features including a sandbox for suspect software, a password vault, and a few bells and whistles such as game mode to block pop ups and browser cleanup tools.
Depending on your budget and your need for more security and tools, Avast could be right for you as it’s got more for a higher price. But for just the basics we recommend Malwarebytes Premium.
Charles Burns, Global Head of Security - New Mobility for Uber, will deliver a keynote address at ISC West 2020.
Internet-enabled crimes and scams show no signs of letting up, according to data released by the FBI’s Internet Crime Complaint Center (IC3) in its 2019 Internet Crime Report.
Sauce Labs Inc., a provider of continuous testing cloud, announced the appointment of Justin Dolly as chief security officer.
The National Science Foundation’s Robert Noyce Teacher Scholarship Program has awarded St. Edward’s University a more than $1.18 million grant for scholarships aimed at recruiting, preparing and supporting middle and high school math and science teachers.
The Phishers' Favorites report for Q4 2019 says that PayPal remains the top brand impersonated by cybercriminals for the second quarter in a row, with Facebook taking the #2 spot and Microsoft coming in third.
The University of Wisconsin-Whitewater will offer one of the first online Master of Science in Cybersecurity programs in the state of Wisconsin to help meet regional demand for protection against cybersecurity attacks.
Taking place across the U.S. and the world, cybersecurity conferences can offer unique opportunities for cybersecurity professionals, such as hands-on workshops, networking and certifications. They also provide cybersecurity leaders with greater security awareness of threats, tactics and best practices needed to effectively thwart attacks on the systems and assets they protect. Here, Security brings you a list of the top 20 cybersecurity conferences in the U.S. in 2020.
Back away from the snooze button. This is a $29 million wake-up call you can’t afford to miss. In January 2019, Yahoo’s board agreed to pay the enormous $29 million settlement to its shareholders as the result of cyberattacks that compromised three billion Yahoo user accounts. It was the first time shareholders had successfully held a company responsible for data breaches. And it is a loud warning to corporate boards that they must start paying attention to cyber risks. But are they? Considering that over 7.9 billion records were exposed as of September 2019 — up 112 percent from 2018 — it looks like they may have their fingers in their ears.
A new report on the working life of the CISO examines the impact of continued stress on the mental health and personal lives of CISOs, and drills down into the causes of stress including poor work life balance and a lack of support from the board.
(ISC)² has entered into a strategic partnership with the Australian Information Security Association (AISA) to jointly work towards a safer and more secure cyber world.
A large majority of election-related websites operated by local governments in battleground states lack a key feature that would help them be more cybersecure.
(ISC)² announced a global call for speakers for its 10th annual Security Congress conference, to be held November 16-18 in Orlando, Fla.
In my December column, I ended with the observation that many CISOs struggle when it comes to first determining and then actually communicating the business value of the security options out there.